Here we can see “How to Make Use of the ss Command on a Linux System”
The ss command is a new take on the original netstat command. On Linux, you can use it to get statistics on your network connections. Here’s how to use this useful tool.
Netstat vs. The ss Command
ss, a successor for the deprecated netstat command, provides extensive information on your computer’s interactions with other computers, networks, and services.
Transmission Control Protocol (TCP), User Datagram Protocol (UDP), Unix (interprocess), and raw socket statistics are displayed by ss. The application program must handle TCP and UDP headers, not the transport layer because raw sockets operate at the network OSI level. Raw sockets are used in both ICMP (Internet Control Message Protocol) packets and the ping application.
Using ss
You don’t need to install ss because it comes pre-installed with most modern Linux distributions. On the other hand, its output can be quite lengthy—we’ve seen outcomes with over 630 lines. The range of outcomes is likewise quite extensive.
As a result, we’ve included text representations of our findings because they wouldn’t fit in a screenshot. Likewise, we’ve cut them down to make them easier to manage.
Connections to the Internet
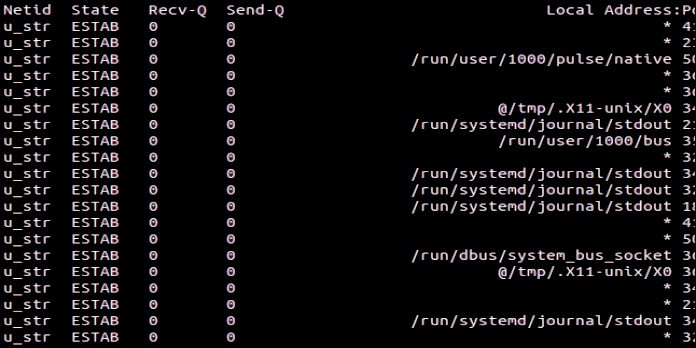
Using ss without any command-line parameters returns a list of non-listening sockets. That is, it displays a list of sockets that aren’t listening.
Type the following into your browser to see this:
ss

Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process u_str ESTAB 0 0 * 41826 * 41827 u_str ESTAB 0 0 /run/systemd/journal/stdout 35689 * 35688 u_str ESTAB 0 0 * 35550 * 35551 ... u_str ESTAB 0 0 * 38127 * 38128 u_str ESTAB 0 0 /run/dbus/system_bus_socket 21243 * 21242 u_str ESTAB 0 0 * 19039 * 19040 u_str ESTAB 0 0 /run/systemd/journal/stdout 18887 * 18885 u_str ESTAB 0 0 /run/dbus/system_bus_socket 19273 * 17306 icmp6 UNCONN 0 0 *:ipv6-icmp *:* udp ESTAB 0 0 192.168.4.28%enp0s3:bootpc 192.168.4.1:bootps
The following are the columns:
- Netid: The type of Socket is referred to as the netid. We have a “u str,” a Unix stream, a “udp,” and an “icmp6,” an IP version 6 ICMP socket in our example. More information on Linux socket types can be found on the Linux man-pages.
- State: The current condition of the Socket.
- Recv-Q: The number of packets received.
- Send-Q: The total number of packets sent.
- Local Address:Port: This is the local address and the port (or equivalent values for Unix sockets).
- Peer Address:Port: The remote address and port are the peer address and port (or equivalent values for Unix sockets).
The “State” field for UDP sockets is normally empty. However, it can be one of the following for TCP sockets:
- Listen: This is a server-only feature. A connection request has been sent to the Socket.
- SYN-SENT: Only for clients. This Socket has requested a connection and is waiting for it to be accepted.
- SYN-RECEIVED: Only on the server. After accepting a connection request, this Socket is waiting for a connection acknowledgment.
- SERVER AND CLIENTS HAVE BEEN ESTABLISHED. In addition, a functioning connection between the server and the client has been established, allowing data to be transmitted between the two.
- FIN-WAIT-1: Clients and server. This Socket is waiting for a connection termination request from the remote Socket or acknowledging a connection termination request sent from this Socket before.
- FIN-WAIT-2: Clients and server This Socket is waiting for the remote Socket to send a connection termination request.
- CLOSE-WAIT: Client and server. This Socket is waiting for the local user to request connection termination.
- THE SERVER AND CLIENTS ARE NOW CLOSED. This Socket is waiting for the remote Socket to acknowledge a connection termination request.
- LAST-ACK: Both the server and the client. This Socket is waiting for the remote Socket to acknowledge the connection termination request has been submitted.
- TIME-WAIT: For both the server and the clients. The remote Socket received an acknowledgment from this Socket, indicating that it had received the remote Socket’s termination request. It is now awaiting confirmation of receipt of the acknowledgment.
- CLOSED: The plug has been closed because there is no connection.
Listening Sockets are listed in alphabetical order.
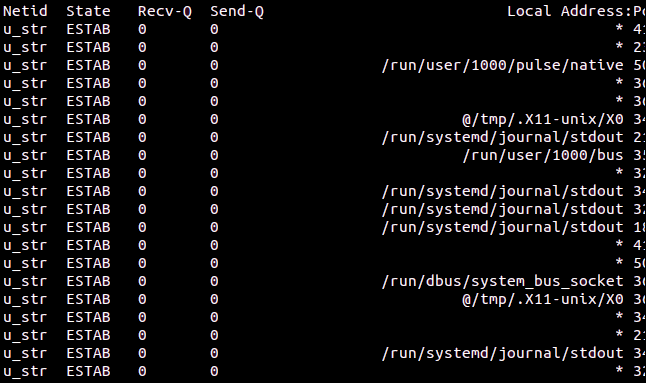
We’ll use the -l (listening) option to see the listening sockets, as follows:
ss -l

Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process nl UNCONN 0 0 rtnl:NetworkManager/535 * nl UNCONN 0 0 rtnl:evolution-addre/2987 * ... u_str LISTEN 0 4096 /run/systemd/private 13349 * 0 u_seq LISTEN 0 4096 /run/udev/control 13376 * 0 u_str LISTEN 0 4096 /tmp/.X11-unix/X0 33071 * 0 u_dgr UNCONN 0 0 /run/systemd/journal/syslog 13360 * 0 u_str LISTEN 0 4096 /run/systemd/fsck.progress 13362 * 0 u_dgr UNCONN 0 0 /run/user/1000/systemd/notify 32303
All of these sockets are open and listening. The term “rtnl” refers to the routing Netlink, which is used to send data between kernel and userspace programs.
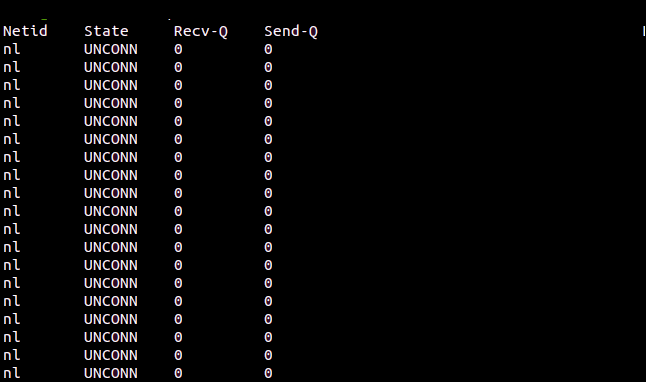
All Sockets are listed in alphabetical order.
The -a (all) option can be used to list all sockets:
ss -a

Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process nl UNCONN 0 0 rtnl:NetworkManager/535 * nl UNCONN 0 0 rtnl:evolution-addre/2987 * ... u_str LISTEN 0 100 public/showq 23222 * 0 u_str LISTEN 0 100 private/error 23225 * 0 u_str LISTEN 0 100 private/retry 23228 * 0 ... udp UNCONN 0 0 0.0.0.0:631 0.0.0.0:* udp UNCONN 0 0 0.0.0.0:mdns 0.0.0.0:* ... tcp LISTEN 0 128 [::]:ssh [::]:* tcp LISTEN 0 5 [::1]:ipp [::]:* tcp LISTEN 0 100 [::1]:smtp [::]:*
All sockets, regardless of condition, are included in the output.
TCP Sockets are listed here
You can also use a filter to view just sockets that fit your criteria. For example, we’ll use the -t (TCP) option to display just TCP sockets:
ss -a -t
UDP Sockets are listed in alphabetical order.
The -u (UDP) option performs a similar filtering operation. We’ll see UDP sockets this time:
ss -a -u
Local Address:Port Peer Address:Port Process State Recv-Q Send-Q
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process UNCONN 0 0 0.0.0.0:631 0.0.0.0:* UNCONN 0 0 0.0.0.0:mdns 0.0.0.0:* UNCONN 0 0 0.0.0.0:60734 0.0.0.0:* UNCONN 0 0 127.0.0.53%lo:domain 0.0.0.0:* ESTAB 0 0 192.168.4.28%enp0s3:bootpc 192.168.4.1:bootps UNCONN 0 0 [::]:mdns [::]:* UNCONN 0 0 [::]:51193 [::]:*
Unix Sockets are listed in alphabetical order.
You can use the -x (Unix) option to observe just Unix sockets, as seen below:
ss -a -x
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process u_str ESTAB 0 0 * 41826 * 41827 u_str ESTAB 0 0 * 23183 * 23184 u_str ESTAB 28 0 @/tmp/.X11-unix/X0 52640 * 52639 ... u_str ESTAB 0 0 /run/systemd/journal/stdout 18887 * 18885 u_str ESTAB 0 0 /run/dbus/system_bus_socket 19273 * 17306
Raw Socket is a list of raw sockets
The -w (raw) option is used to filter raw sockets:
ss -a -w
Sockets for IP Version 4
The -4 (IPV4) option can be used to list sockets that use the TCP/IP version 4 protocol:
ss -a -4
Sockets for IP Version 6 are listed below
With the -6 (IPV6) option, you can enable the matching IP version 6 filter, as follows:
ss -a -6
State-by-State Socket Listing
With the state option, you can sort sockets by their current state. This works in the following states: established, listening, and closed. We’ll also employ the resolve option (-r), which attempts to map network addresses to names and ports to protocols.
The following program will seek for TCP connections that have already been established, and ss will attempt to resolve the names:
ss -t -r state established
Four connections have been formed. The hostname, ubuntu20-04, has been resolved, and the SSH connection on the second line now displays “ssh” rather than 22.
To look for sockets in the listening state, we can repeat the process:
ss -t -r state listening
Recv-Q Send-Q Local Address:Port Peer Address:Port Process 0 128 localhost:5939 0.0.0.0:* 0 4096 localhost%lo:domain 0.0.0.0:* 0 128 0.0.0.0:ssh 0.0.0.0:* 0 5 localhost:ipp 0.0.0.0:* 0 100 localhost:smtp 0.0.0.0:* 0 128 [::]:ssh [::]:* 0 5 ip6-localhost:ipp [::]:* 0 100 ip6-localhost:smtp [::]:*
Sockets by Protocol is a list of sockets organised by protocol
The dport and sport parameters, which represent the destination and source ports, respectively, can enumerate the sockets that use a specific protocol.
To list sockets on an established connection using the HTTPS protocol, type the following (notice the space after the opening parenthesis and before the closing one):
ss -a state established ‘( dport = :https or sport = :https )’
We can use the protocol’s name or the port that is often associated with it. For example, Secure Shell (SSH) uses port 22 as its default.
In one command, we’ll use the protocol name; in the next, we’ll use the port number:
ss -a ‘( dport = :ssh or sport = :ssh )’
ss -a ‘( dport = :22 or sport = :22 )’
We received the same results as predicted.
Connections to a Specific IP Address are listed here
We can list connections to a specific destination IP address using the dst (destination) parameter.
The following is what we type:
ss -a dst 192.168.4.25
Processes to Be Recognized
You can use the processes option (-p) to view which processes are using the sockets, as demonstrated below (notice that sudo is required):
sudo ss -t -p
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
ESTAB 0 0 192.168.4.28:57650 54.218.19.119:https users:(("firefox",pid=3378,fd=151))
ESTAB 0 0 192.168.4.28:ssh 192.168.4.25:43946 users:(("sshd",pid=4086,fd=4),("sshd",pid=3985,fd=4))
The SSH daemon and Firefox use the two established TCP socket connections, as evidenced by this.
A Deserving Successor
The ss command delivers the same information as netstat but in a more user-friendly and accessible style. More options and tips can be found on the man page.
Conclusion
I hope you found this information helpful. Please fill out the form below if you have any queries or comments.
User Questions:
1. What is the purpose of the SS command in Linux?
To dump socket statistics, use the ss command. It allows you to display information in a similar way to netstat. Other tools can’t display as much TCP and status information as this one can.
2. What does the SS command stand for?
The ss command dumps socket statistics and shows information in a similar (but simpler and faster) manner to netstat. Most other tools can’t display as much TCP and state information as the ss command does.
3. What exactly is an IP port?
To do so, type “netstat -a” into Command Prompt and press Enter. A list of your active TCP connections will appear. After the IP address, the port numbers will be displayed, separated by a colon. For example, if your IP address is 192.168.
4. In Linux, how do I read a socket file?
Alternatively, you can use the lsof command. The command lsof, which stands for “list open files,” is used on many Unix-like systems to display a list of all open files as well as the processes that opened them.
5. What exactly is SS?
What is SS? from Kalilinux