Winpot Atm Malware Download into Slot Machines.
BREAKING!
Kaspersky back at it again, exposing significant cybercriminals!!! Ok, jokes aside, this piece of malware has all the news outlets going bananas, dubbed “WinPot”, an ATM payload that causes the machine to spew money, sort of a casino coin machine.
Similar to another piece of malware, we covered a short time back called Ploutus-D. I’m thinking everyone forgot at some point that the majority of ATMs, especially those running in certain Third World countries, still run Windows XP! Yes, that’s correct. Your assets are super secure sitting inside some random XP box. You’d think a bank has everything covered.
So, where did this malware come from? I traced it back to a forum (that’s not on the darknet like how most outlets are reporting) after an easy Google search, called “club2crd”. the primary regard to WinPot I found on this forum dates to 8/18/2018 by a user named “Muhammad98” selling it for USD 1000. This version of WinPot (rather old) targets Wincor ATM’s specifically manufactured by Nixdorf, an equivalent brand of ATMs that the Ploutus-D malware targets.
Another regard to WinPot (this time version 3) dates back to 12/9/2018. The user who goes by the alias “wav”, who also appears to be a Senior Member (yes, he’s super 1337), was selling the trojan for 1 BTC (during the time, worth USD 6440.52). I don’t even think half these forums sit and believe the worth of their tool, and I feel that “1 BTC” is typically just a random arbitrary number they throw at almost everything they’re sitting on. That old CC dump? Yea that’s 1 BTC. Don’t take my word for it, but this piece of malware is nowhere on the brink of six thousand dollars.
After further complicated Google search queries, I found another strand of malware that’s built off of WinPot, dubbed “Annuit Coeptis” (Illuminati reference) that does exactly what WinPot does, only priced at 500 dollars.
The person selling this version is additionally Muhammad98, an equivalent one that sold the prior version of WinPot. What’s different? No clue. Supported the screenshot, the functionality is identical. Then after five minutes, I discovered a forum reply stating that the program doesn’t even work! It crashes thanks to the shortage of proper coding skills by its author. Below you’ll find a video of the WinPot malware fully use on an unsuspected ATM.
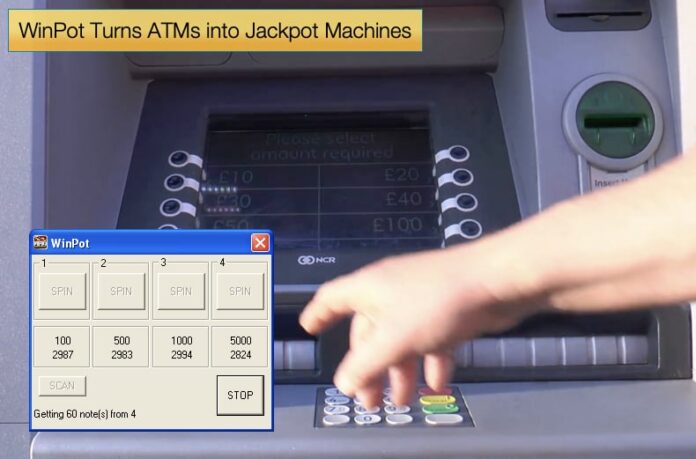
ATM-jackpotting WinPot malware now features a slot machine interface
- Winpot Atm Malware Download, is meant to compromise the ATMs and force them to empty their cassettes of all funds.
- WinPot is an ATM malware that uses a coin machine interface to steal funds by compromising ATMs.
Researchers analyzed a replacement malware sample dubbed WinPot, which first appeared in underground forums in March 2018. WinPot is an ATM malware that uses a coin machine interface to steal funds from ATMs. WinPot, also referred to as ATMPot, is meant to compromise the ATMs and force them to empty their cassettes of all funds.
Slot machine interface
The cybercriminals behind the WinPot malware have worked hard on the interface to form it appear as if that of a coin machine is probably going regarding the favoured term ATM-jackpotting.
The WinPot interface includes a visible indicator of an ATM’s cassettes.
- Each cassette features a reel of its own numbered 1 to 4, where 4 is the maximum number of cash-out cassettes in an ATM.
- Each cassette also has buttons labelled SPIN, SCAN, SLOT, and STOP.
- Once victims press the SPIN button, the ATM starts dispensing cash from the respective cassette.
- The SCAN button rescans the ATM and updates the numbers under the SLOT button.
- Pressing the STOP button stops dispensing cash from the machine.
Modifications made to WinPot
While researchers from Kaspersky Lab were analyzing the WinPot sample, they observed more new models with modifications.
The malware seller has recently offered WinPot v. three, which incorporates a revamped interface and a currently unidentified program called ‘ShowMeMoney’ almost like the coin machine interface. The mechanism looks almost like Cutlet Maker malware.
WinPot authors make modifications to the malware for subsequent reasons,
- New samples with new modifications are made to WinPot to trick the ATM security systems.
- Modifications are made to the malware to detect new methods to keep the cash mules from abusing WinPot.
- Modifications are made to beat potential ATM limitations and to enhance the interface and error-handling routines.
“We thus expect to ascertain more modifications of the prevailing ATM malware. the well-liked way of protecting the ATM from this type of threat is to possess device control and process whitelisting software running thereon. the previous will block the USB path of implanting the malware directly into the ATM PC. At the same time, the latter will prevent the execution of unauthorized software thereon,” researchers wrote during a blog.