Whether you are a small, midsize, or large company, a Cybersecurity Lifecycle can be costly and even deadly to your company’s survival. A good instance is that the ransomware assault in an Arkansas-based telemarketing business allegedly had to close down operations and lay off 300 workers.
To prevent a similar tragedy, you need to build a safety program that may help your teams identify and respond to cyber threats. To do so, you can consult with the National Institute of Standards Technology (NIST) framework, which according to Gartner, can be employed by 73 percent of organizations globally (total content readily available to customers only).
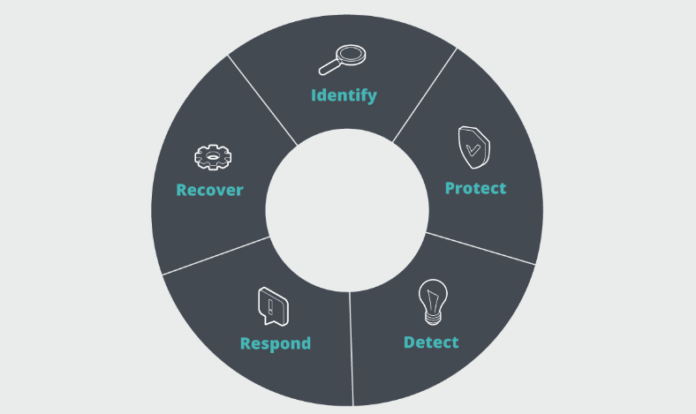
Within the following guide, we will describe how to make a more 5-phase cybersecurity lifecycle frame that may holistically enhance your company’s security position.
1. Identify: Assess the security risk
After identification of these community securities and vulnerabilities, now it is the opportunity to shield your system. This stage from the Cybersecurity Lifecycle can also be known as mitigating location as this alleviates the danger identified. The machine here needs to be drawn following the business policies and principles. Awareness about different techniques offered in business ought to be developed in one of the groups. This may be accomplished via a set of training.
- Access management — Knowing the numerous levels of accessibility and permits.
- Data Security — Supplying the safety for the Information to be shielded.
- Information Protection and processes — Information about processing storage and transmission of sensitive info.
- Care — Routine tests for maintaining a particular condition.
- Protective Tech — Technologies are shielding your platform environment.
2. Protect: Implement security measures
Regardless of what degree of security a system might happen, with the rising threat now, it might have compromised at any given amount. In the detection stage, the system can identify attack signatures and establish the degree of actions completed. The cybersecurity Lifecycle ought to be able to determine regular and malicious activities. This is sometimes considered equally enjoy the fire alarm in our workplaces or houses. It finds the flame a few seconds and throws alerts into an environment. IDS (Intrusion Detection System) should have the ability to guess the intrusion after it’s occurred. It ought to continue to keep a good look at the strikes originated from inside the computer system. After factors could be considered for precisely the same.
- Anomalies and occasions — Deciding monsters at mid-degree is the top job of boundary level alternative if this fails, the whole system is a playground for the attacker.
- Security continuous observation: — The alternative needs to have actual-time threat monitoring capacity.
- Detection procedure: — the iterative process of locating anomalies or risks ought to be quite fast. It must correlate all risks back to thing; therefore, SOC analysts could incorporate monsters in their risk library.
3. Detect: Monitor threats proactively
Timely actions are central to shielding the system from strikes. Considering our case of fire alarms in the event, the crucial steps that aren’t taken while the fire has happened would lead to a massive reduction of funds. Similarly, if timely activities aren’t removed from the attacks, it could lead to a more significant decrease in data hampering the whole company and environment. Policies against such Cybersecurity Lifecycle ought to be accessible prior so that timely action may be potential. Prioritization of unique varieties of hazard levels and activities against them must be identified clearly.
A Computer Security Incident Response Team (CSIRT) needs to be able to coordinate and handle all of the tasks from discovery to the documentation of this occurrence. Concisely, the under points could be contemplated.
- Incident Respond Planning: — Organizing management is a procedure of reporting a company’s events to identify, assess, and fix risk to protect against a succeeding re-occurrence.
- Incident Communications: — Communication is critical for virtually any incident response period. Including incident response staff source, direction, and the overall employee base. Sharing info using Computer Security Incident Response Team (CSIRT) about details encircle the episode at the proper level, Incident period and depriving them of the responsibilities to keep the confidentiality of some useful info can disperse hearsay. It will also assist in predictive intellect and decrease the danger of data being exfiltrated in the company.
- Cyber Incident Evaluation: ” In event analysis analyst should begin with endpoint system investigation; the attacker might have left some backdoor or assault vector for much additional harm. An individual ought to analyze all customers, entities of organizational resources and attempt to seek out anomalies. If you discover no satisfactory outcomes, then the security adviser can involve a danger searching team to execute an in-depth dip investigation on logs and connect various data sources.
- Incident Mitigation: — Incident Mitigation is the simple procedure of restricting attack surface to get attacker and implementing situational controls according to all indications of compromises and enforcing new coverages to safety options.
- Incident Improvements Procedure: — It’s a continually evolving cycle; within this stage, CSIRT should treat Incident Reporting, Tracking IOC for a while, and developing behavioral evaluation on that. Update all-hazard intellect feeds and requires preventative steps for many actionable items. Document each action required by CSIRT to ensure this info will be quite useful for future cyber events.
4. Respond: Create a response plan
Timely actions are central to shielding the system from strikes. Considering our case of fire alarms in the event, the crucial steps that aren’t taken while the fire has happened would lead to a massive reduction of funds. Similarly, if timely activities aren’t removed from the attacks, it could lead to a more significant decrease in data hampering the whole company and environment. Policies against such Cybersecurity Lifecycle ought to be accessible prior so that timely action may be potential. Prioritization of unique varieties of hazard levels and activities against them must be identified clearly.
A Computer Security Incident Response Team (CSIRT) needs to be able to coordinate and handle all of the tasks from discovery to the documentation of this occurrence. Concisely, the under points could be contemplated.
- Incident Respond Planning: — Organizing management is a procedure of reporting a company’s events to identify, assess, and fix risk to protect against a succeeding re-occurrence.
- Incident Communications: — Communication is critical for virtually any incident response period. Including incident response staff source, direction, and the overall employee base. Sharing info using Computer Security Incident Response Team (CSIRT) about details encircle the episode at the proper level, Incident period and depriving them of the responsibilities to keep the confidentiality of some useful info can disperse hearsay. It will also assist in predictive intellect and decrease the danger of data being exfiltrated in the company.
- Cyber Incident Evaluation: ” In event analysis analyst should begin with endpoint system investigation; the attacker might have left some backdoor or assault vector for much additional harm. An individual ought to analyze all customers, entities of organizational resources and attempt to seek out anomalies. If you discover no satisfactory outcomes, then a safety analyst may involve danger hunting staff to execute in-depth dip analysis on logs and correlate various information sources.
- Incident Mitigation: — Incident Mitigation is the simple procedure of restricting attack surface to get attacker and implementing situational controls according to all indications of compromises and enforcing new coverages to safety options.
- Incident Improvements Procedure: — It’s a continually evolving cycle; within this stage, CSIRT should treat Incident Reporting, Tracking IOC for a while, and developing behavioral evaluation on that. Update all-hazard intellect feeds and requires preventative steps for many actionable items. Document each action required by CSIRT to ensure this info will be quite useful for future cyber events.
5. Recover: Ensure business continuity
Timely retrieval is only putting the whole compromised position of business back to the manufacturing atmosphere. We could predict this as the previous point at the Cybersecurity Lifecycle. This assists in regaining and protecting a company from tragedy. Documentations also have to be considered to be able to comprehend the loopholes and advancement places.
Recovery Planning- it is a long-term process that goes via constant phases of progress. According to the previous lessons learned, business stimulation can be struck and consequently could be operated upon. The whole team working together ought to comprehend the organization’s technology, procedures, interacting groups, protocols, dependence maps, and reason for every implementation program.