What is a Cybersecurity Risk Assessment?
Cybersecurity Risk Assessment is characterized by NIST as dangers assessments are utilized to identify, quote, and reevaluate hazards to organizational operations, organizational resources, people, other associations, along with the Nation, resulting in the performance and usage of data systems.
A cyber risk assessment's main intention will be to help notify decision-makers and encourage appropriate risk...
we created and posted a ffiec Cybersecurity Assessment Tool xls into action by tracking your responses
Overview for Chief Executive Officers and Boards of Directors
In light of this increasing quantity and sophistication of cyber threats, the Federal Financial
Institutions Evaluation Council1 created the FFIEC Cybersecurity Assessment Tool xls.
(Assessment) on behalf of its members, to assist institutions in identifying their risks and deciding
Their...
Given that the genuine and current cybersecurity risks, organizations need always to maintain heightened security consciousness to secure their critical data and resources. Concerning national organizations and agencies that handle their information, this translates into implementing useful security controllers and different IT methods to guard resources and secure infrastructure. TDI is near Knowledgeable about the related Assessment & Authentication...
Even the nonpartisan Aspen Cybersecurity Group was created to alter how our electronic society oversees technology's dangers. By providing a unique, multidisciplinary forum for fair dialogue between policymakers, industry executives, safety specialists, and civil society leaders, the Group forges lasting and new partnerships that may operationalize practical answers to the many pressing cybersecurity issues. Its Existing workstreams Concentrate on:
Education...
Cybersecurity
Health Industry Cybersecurity Practices Managing Threats and Protecting Patients
admin - 0
Health Industry Cybersecurity Practices Managing Threats and Protecting Patients (HICP), the principal book of this Cybersecurity Act of 2015, Section 405(d) Task Group, intends to improve awareness, supply Qualifications cybersecurity practices, and also proceed associations towards consequences in simplifying the present most applicable cybersecurity risks to the industry. It attempts to help health care and public health organizations to...
Best Cybersecurity for Small and Medium Enterprises
How does your company avoid being a casualty of a cyber-attack? Listed below are just eight Cybersecurity for Small and Medium Enterprises for the company it's possible to start to execute now.
1. Use a firewall
Among the very first lines of defense at a cyber-attack is that a firewall. Even the Federal Communications Commission...
What is a red team
In a Red Team Exercise Cybersecurity simulation, this red group functions as an adversary, recognizing and exploiting potential weaknesses in the business's cyber defenses utilizing complex attack methods. These offensive teams typically include highly knowledgeable safety specialists or individual ethical hackers concentrating on penetration testing by copying real-world assault methods and methods.
The red team increases...
CCI (Control Correlation Identifiers) - A better baseline framework
CCI Cybersecurity tackles the complex issues of NIST by dividing down controls into more manageable components. There are over 3,000 CCI controllers, but it does not mean there's much more work to perform. It only implies every control specifies one necessity, making risk management and compliance jobs more straightforward to carry...
Whether you are a small, midsize, or large company, a Cybersecurity Lifecycle can be costly and even deadly to your company's survival. A good instance is that the ransomware assault in an Arkansas-based telemarketing business allegedly had to close down operations and lay off 300 workers.
To prevent a similar tragedy, you need to build a safety program that may...
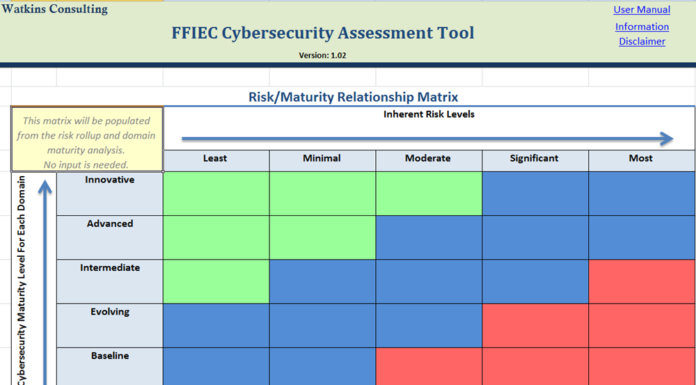
WHAT IS THE FFIEC CYBERSECURITY ASSESSMENT TOOL?
The FFIEC Cybersecurity Assessment Tool (CAT) is a diagnostic test which aids associations to identify their danger level and ascertain the maturity of the cybersecurity applications.
The FFIEC's tool steps danger levels across several classes, such as delivery stations, link types, external dangers, and organizational attributes. In the end, the tool enables management to...